EVE Online: Odyssey is coming on the 4th of June and Exploration as a profession is seeing a lot of love from the developers at CCP. Team Prototyping Rocks has been working hard on improving the depth of gameplay that explorers will enjoy in their day to day lives. The devil is in the details and until this release the details behind Hacking and Archaeology have been very sparse. Our brief was to make the tasks you do in sites much more immersive and interactive. In other words, to remove the "sit and wait" aspect of Exploration gameplay and replace it with something interesting to do.
How Hacking Will Work
Our approach to this task was to start with what we know best, prototype creation. This let us come up with ideas for mechanics without investing an awful lot of time. Our final feature design came together as a card game. The feature itself takes the mechanics similar to those found in exploration based dungeon crawlers, roguelikes, etc., and gives them a hacking twist. We like this because it furthers the feeling of exploring unknown, hazardous places in the computer system controlling the object you are hacking. We hit most of the roguelike tropes, with procedurally generated levels, turn based combat and "permadeath" - albeit on a scale that is suited to shorter games.
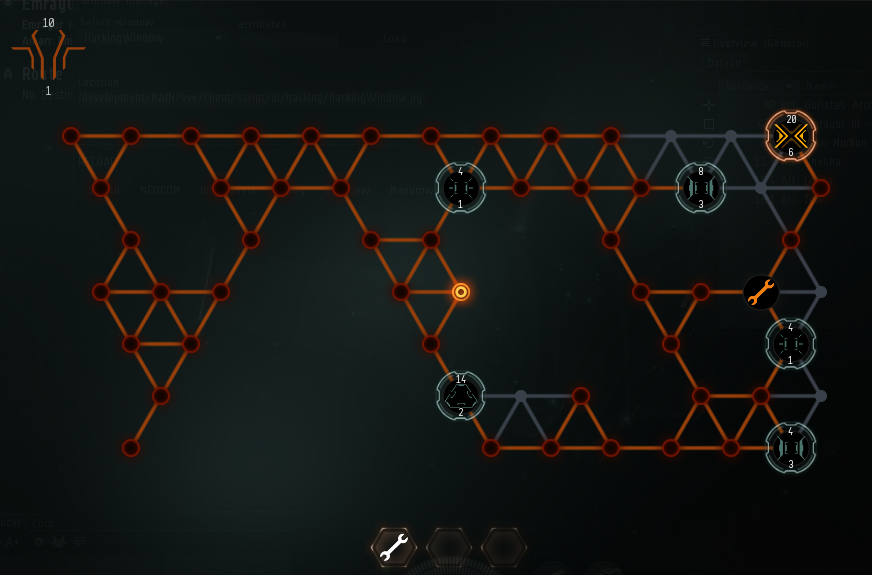
This work in progress image shows a Hacking attempt in progress, although the hacker in this case faces a pretty stiff challenge to defeat this System Core.
The player begins by activating their Hacking or Archaeology module on the appropriate target and is then presented with the UI window for their module. The gameplay remains the same between both Hacking and Archaeology with the latter being appropriately themed as an older computer system both visually and aurally. The window shows the user the computer system mapped out as a network of interconnected nodes. One of the node's contents is already visible as this was the penetration point of the activated module. Users hack a system by exploring the nodes adjacent to the nodes that they have already explored. Their goal is to find the core or cores in the system and taking them over by destroying them. Once the core is destroyed the system has been hacked and the module forces the site to scatter its contents from the cargo hold into the vacuum of space. The hacker, his friends and anyone else around can then collect the scattered contents. We'll be releasing another devblog shortly that will go into details of how the contents of the site are distributed and how they are collected.
Along the way users are going to encounter a variety of different subsystems:
Defense Subsystems
These are the protectors of the system, once uncovered they prevent the module from spreading to nodes adjacent to it. Some advanced defense subsystems also have other abilities to confound attackers.
Utility Subsystems
Scattered throughout the computer system are various utilities that the user can take and either use to bolster their module or attack defense subsystems and the cores.
Datacaches
These encrypted nodes are typically benign. The user can choose to decrypt the node to discover its contents. This might uncover a great utility or it might bring some particularly nasty defense subsystem online.
Cores
Mentioned above already these are the heart of the system being hacked. Destroy all the cores in a system and you gain control.
The modules, defense subsystems and cores have attributes that define their coherence (hit points) and strength. Combat is resolved through the attacker going first. The defender's coherence is reduced by the attacker's strength and visa-versa if the defender survives.
Modules also have a number of utility slots, this limits the number of active utilities that a module can have at a time.
A hacking attempt is failed when the module loses coherence in the system. Fail too many times and the system will self-destruct the object destroying all its contents. Hacking attempts can also be failed by flying too far away from the object being hacked, by taking too long and being kicked out of the system or by closing the module UI. On top of which only one person can hack an object at a time.
Modules and Skills
EVE's Team Superfriends are working on broader changes to Exploration and are supporting us in updating the modules that you will be using. All existing modules and skills have been mapped over to this new system so those who have already trained them will have similar advantages that they currently enjoy.
The Future
This first release of changes to Hacking and Archaeology are just the tip of the iceberg. In the future we hope to add in much more variety into the subsystems you encounter whilst hacking. We would like to add some rare, unique things for hackers to find and interact with.
We also need to tie the Hacking activity much closer into the EVE Universe. To do so we are going to find a way for hackers to pre-prepare themselves for hacking and gain items useful for Hacking from engaging in the activity itself. This may be allowing hackers to retrieve unused utilities and sell them on the market or create them themselves through some form of production line from data resources gathered whilst hacking. Either way we want to open up the Hacking experience to the economy of EVE.
We'd also like to expand the variety and complexity of things that you can hack in EVE to bring it out of its current niche and into the wider world, allowing us to create situations where hackers are valuable for more than just their ability to gain ISK.
Lots of people have asked about competitive or cooperative hacking and that's something that we may well explore but for now we wish to deepen the current experience and how it connects into EVE.
Last modified on Thursday, 30 May 2013 09:34